
McAfee Application Control (Solidcore) XML Generator PowerShell Script
If you want to quickly generate a XML file for importing in to McAfee Application Control (Solidcore) as allowed hashes then you can use this PowerShell script. It will scan a folder and output a XML file which can then be imported in to McAfee ePO. I wrote this up as it was needed to add hashes for a whole bunch of folders. I know you shouldn't be doing this in McAfee Application Control (Solidcore) but sometimes you have to. It will generate the SHA1 and SSHA256 hashes for each of the following files types: .vbs; .exe; .ps1; .psm1; .bat; .dll.
Steps
- Copy code from below to PowerShell ISE
- Edit the $scan_path & $Path
- Run
- It opens notepad with the file so you can have a quick check before uploading
- Log in to McAfee ePO
- Solidcore Rules -> Import -> select the file
- DONE
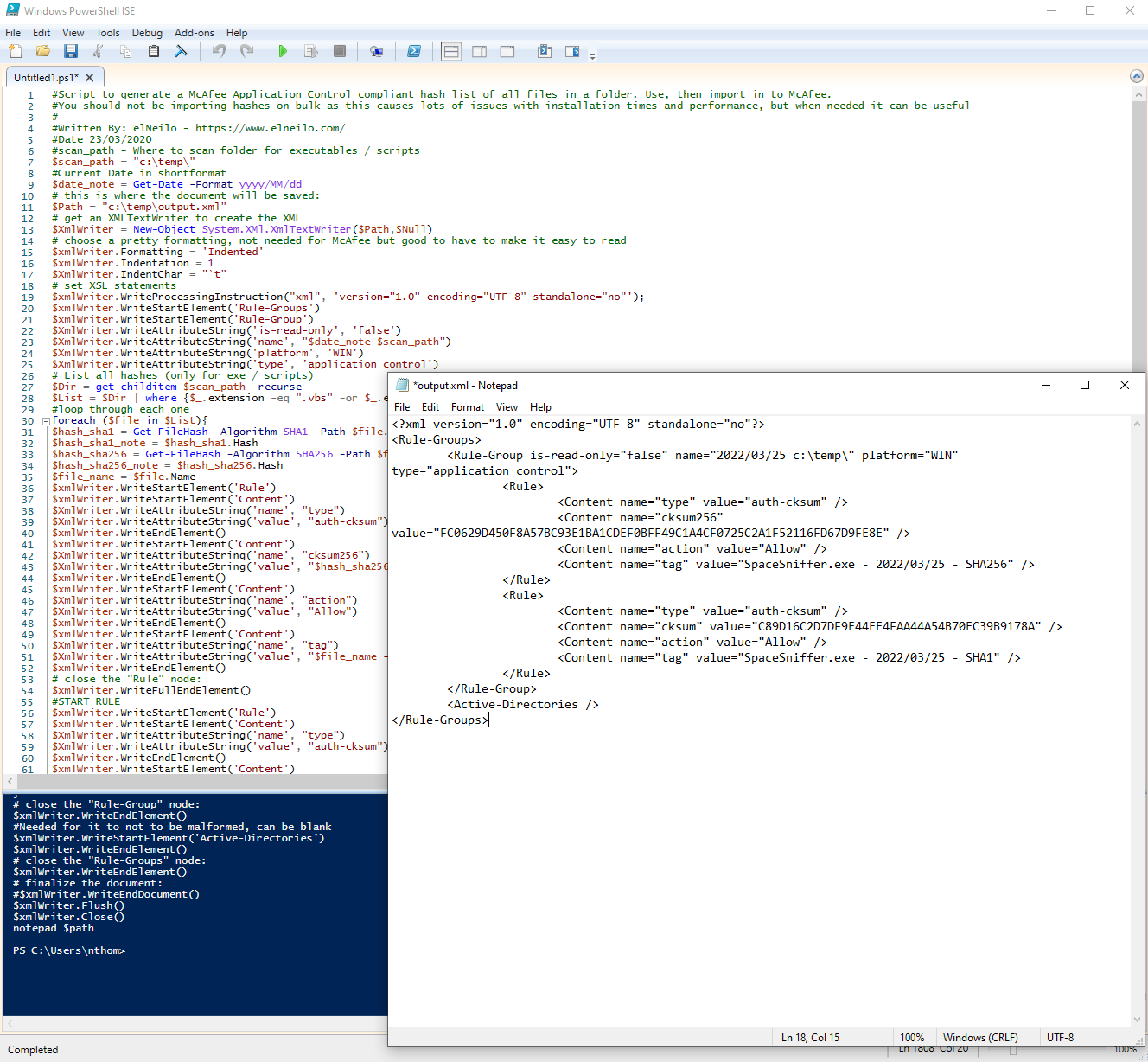
#Script to generate a McAfee Application Control compliant hash list of all files in a folder. Use, then import in to McAfee.#You should not be importing hashes on bulk as this causes lots of issues with installation times and performance, but when needed it can be useful##Written By: elNeilo - https://www.elneilo.com/#Date 23/03/2020#scan_path - Where to scan folder for executables / scripts$scan_path = \\server\share\path\folder#Current Date in shortformat$date_note = Get-Date -Format yyyy/MM/dd# this is where the document will be saved:$Path = "C:\output.xml"# get an XMLTextWriter to create the XML
$XmlWriter = New-Object System.XMl.XmlTextWriter($Path,$Null)# choose a pretty formatting, not needed for McAfee but good to have to make it easy to read$xmlWriter.Formatting = 'Indented'$xmlWriter.Indentation = 1$XmlWriter.IndentChar = "`t"# set XSL statements$xmlWriter.WriteProcessingInstruction("xml", 'version="1.0" encoding="UTF-8" standalone="no"');$xmlWriter.WriteStartElement('Rule-Groups')$xmlWriter.WriteStartElement('Rule-Group')$XmlWriter.WriteAttributeString('is-read-only', 'false')
$XmlWriter.WriteAttributeString('name', "$date_note $scan_path")$XmlWriter.WriteAttributeString('platform', 'WIN')$XmlWriter.WriteAttributeString('type', 'application_control')# List all hashes (only for exe / scripts)
$Dir = get-childitem $scan_path -recurse$List = $Dir | where {$_.extension -eq ".vbs" -or $_.extension -eq ".exe" -or $_.extension -eq ".ps1" -or $_.extension -eq ".psm1" -or $_.extension -eq ".bat" -or $_.extension -eq ".dll" -or $_.extension -eq ".vbs" }#loop through each oneforeach ($file in $List){$hash_sha1 = Get-FileHash -Algorithm SHA1 -Path $file.FullName$hash_sha1_note = $hash_sha1.Hash$hash_sha256 = Get-FileHash -Algorithm SHA256 -Path $file.FullName$hash_sha256_note = $hash_sha256.Hash$file_name = $file.Name$xmlWriter.WriteStartElement('Rule')$xmlWriter.WriteStartElement('Content')$XmlWriter.WriteAttributeString('name', "type")$XmlWriter.WriteAttributeString('value', "auth-cksum")$xmlWriter.WriteEndElement()$xmlWriter.WriteStartElement('Content')$XmlWriter.WriteAttributeString('name', "cksum256")$XmlWriter.WriteAttributeString('value', "$hash_sha256_note")$xmlWriter.WriteEndElement()$xmlWriter.WriteStartElement('Content')$XmlWriter.WriteAttributeString('name', "action")$XmlWriter.WriteAttributeString('value', "Allow")$xmlWriter.WriteEndElement()
$xmlWriter.WriteStartElement('Content')$XmlWriter.WriteAttributeString('name', "tag")$XmlWriter.WriteAttributeString('value', "$file_name - $date_note - SHA256")$xmlWriter.WriteEndElement()# close the "Rule" node:$xmlWriter.WriteFullEndElement()#START RULE$xmlWriter.WriteStartElement('Rule')$xmlWriter.WriteStartElement('Content')$XmlWriter.WriteAttributeString('name', "type")$XmlWriter.WriteAttributeString('value', "auth-cksum")$xmlWriter.WriteEndElement()$xmlWriter.WriteStartElement('Content')$XmlWriter.WriteAttributeString('name', "cksum")$XmlWriter.WriteAttributeString('value', "$hash_sha1_note")$xmlWriter.WriteEndElement()$xmlWriter.WriteStartElement('Content')$XmlWriter.WriteAttributeString('name', "action")$XmlWriter.WriteAttributeString('value', "Allow")$xmlWriter.WriteEndElement()$xmlWriter.WriteStartElement('Content')$XmlWriter.WriteAttributeString('name', "tag")$XmlWriter.WriteAttributeString('value', "$file_name - $date_note - SHA1")$xmlWriter.WriteEndElement()# close the "Rule" node:$xmlWriter.WriteFullEndElement()}# close the "Rule-Group" node:$xmlWriter.WriteEndElement()#Needed for it to not to be malformed, can be blank$xmlWriter.WriteStartElement('Active-Directories')$xmlWriter.WriteEndElement()# close the "Rule-Groups" node:$xmlWriter.WriteEndElement()# finalize the document:#$xmlWriter.WriteEndDocument()$xmlWriter.Flush()$xmlWriter.Close()notepad $path

Please Leave Comments